CLASS Multifactor Authentication replaces the outdated standard of putting the CLASS website behind an IP whitelist.
This is replaced by utilising Microsoft Authentication (aka Azure Active Directory, or AAD) in order to grant access, which has resulted in these changes to how CLASS works:
Release date: 4 December 2021.
If you have any feedback or questions about any of this release, please email the CLASS helpdesk. We are committed to a process of continuous improvement and providing features that meet the needs of Centres, their staff and volunteers.
There is more detailed information about user management under the “User Management and Access” header below.
You can download the Microsoft Authenticator here.
If you have questions about MFA methods, you should speak to your IT.
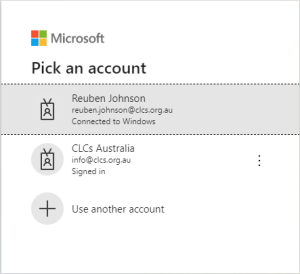
Users will be presented with a new login screen.

CLASS would previously ask users to provide the answers to two security questions upon first login. This is an extremely outdated form of security and has been switched off.
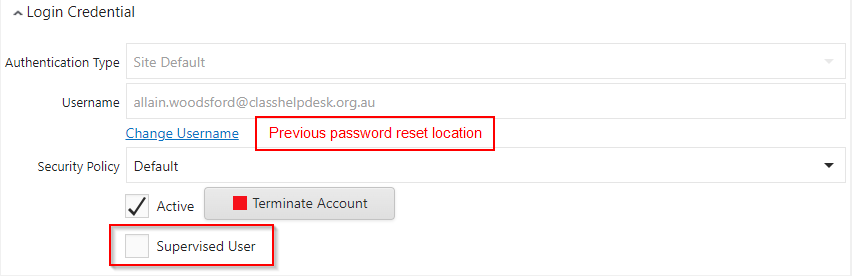
The only way an Azure Active Directory account can be used to authenticate into CLASS requires a CLASS Administrator at your Centre to:
Conversely, if the Centre CLASS Administrator has created a CLASS account, the user cannot access CLASS unless:
The Azure Active Directory section provides more information on types of AAD accounts that can be used under which circumstances.
Security features intended to lock out users under different undesirable scenarios still exist.
It will remain the responsibility of the Centre CLASS Administrator to unlock these users, and the same principles referred to in our user management guide apply.
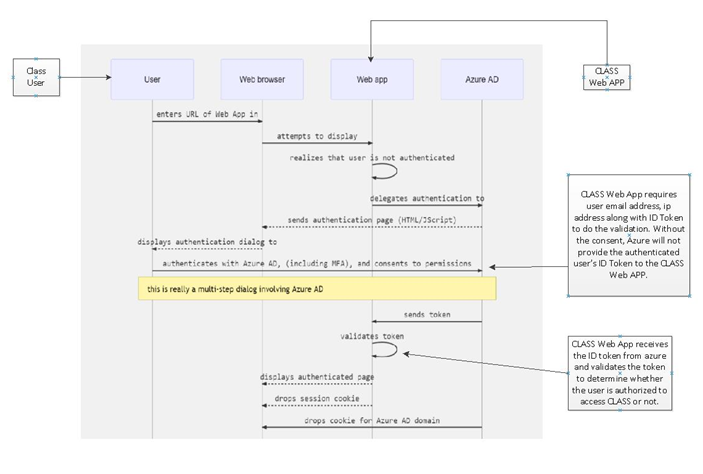
At this stage Azure Active Directory is the only supported authentication method into CLASS.
Some other identity platforms such as Google may allow you to perform a sync from their directory to your Azure Active Directory with an integration and you should work with your IT professional to work through this.
Azure Active Directory supports a number of different additional security factors, and you can even implement your own temporal one time token generator.
We do not advocate for one method above another, but we strongly recommend all users who have access to sensitive information or who have email accounts are secured with at least one additional authentication factor.
Azure has two main types of users:
Whether a user is a member or guest, and if a member user is unlicensed or not can have a few impacts on CLASS access.
A member user who is under an appropriate Azure Active Directory License:
A member user who is not under an appropriate Azure Active Directory License:
A guest user:
Note that usernames must be unique across all of CLASS so if someone is already accessing another CLASS database using their email, you will get an error if you try and create a CLASS account with the same email after inviting them as a guest user.



Community Legal Centres Australia acknowledges the traditional owners of the lands across Australia and particularly acknowledges the Gadigal people of the Eora Nation, traditional owners of the land on which the Community Legal Centres Australia office is situated. We pay deep respect to Elders past, present and emerging.

Community Legal Centres Australia is a proudly inclusive organisation and an ally of the LGBTIQ+ community and the movement toward equality.
ABN 67 757 001 303 ACN 163 101 737
Disclaimer | Privacy Policy
© Community Legal Centres Australia 2022 | Designed by DropIn Solutions